The United States Cyber Command (USCYBERCOM) is a unified combatant command of the United States Department of Defense responsible for planning, organizing, integrating, and synchronizing operations to defend the nation’s networks, systems, and information against cyber threats. Established in 2009 as part of the U.S. Strategic Command, USCYBERCOM became an independent unified combatant command on May 21st, 2018.
USCYBERCOM enables commanders-in-chief to direct cyber forces to ensure freedom of action while operating securely and defending networks from malicious actors on behalf of the American people. It serves as a force-enabling element supporting all functional components within DoD, providing centralized direction and focus for DoD’s cyberspace operations when conducting joint operations with other services or departments such as Homeland Security or FBI.
USCYBERCOM’s main mission is to deter adversaries from conducting malicious activities online by leveraging three key capabilities: intelligence gathering; integration and synchronization; and operational execution in cyberspace operations that support national objectives.
Role and Responsibilities of Cyber Command

Cyber Command (CYBERCOM) is a unified combatant command of the U.S. Department of Defense that is responsible for defending the nation from cyber-attacks and coordinating cyberspace operations. It was established in 2009 to provide centralized command and control for all Department of Defense cyberspace operations, as well as to synchronize defense efforts with other government agencies and international partners.
The Role of CYBERCOM is to protect the nation’s information networks by detecting, preventing, disrupting, and defeating adversaries in cyberspace. CYBERCOM has operational responsibility over the military services’ forces that are used to defend their networks, including those run by the Army, Navy, Air Force, and Marine Corps. In addition, they may direct offensive operations against hostile cyber actors when authorized by law or policy.
The main responsibilities of CYBERCOM include developing strategies to counter threats; conducting intelligence activities; monitoring potential vulnerabilities; analyzing potential threats; countering malicious activity; protecting critical infrastructure networks; providing support for military exercises and contingency plans related to cybersecurity.
History and Evolution of Cyber Command
Since its inception in 2009, the United States Cyber Command (USCYBERCOM) has become an integral part of the military’s ability to combat cyber threats. The command is responsible for defending the nation’s military networks and critical infrastructure from malicious actors. With a mandate of “defending America and its interests in cyberspace,” USCYBERCOM has played a key role in protecting computer networks, counteracting foreign adversaries, and developing defensive capabilities.
The modern history of USCYBERCOM began with the Department of Defense Directive 5105.85 in 2009 which established it as a sub-unified command under US Strategic Command (USSTRATCOM). It was given an initial mission to “plan, coordinate, integrate, synchronize and conduct activities to deter adversaries; ensure freedom of action; provide integrated kinetic/non-kinetic options; defend forward; hunt forward on networks globally; respond decisively when U.S. networks are attacked or compromised.”
Organizational Structure
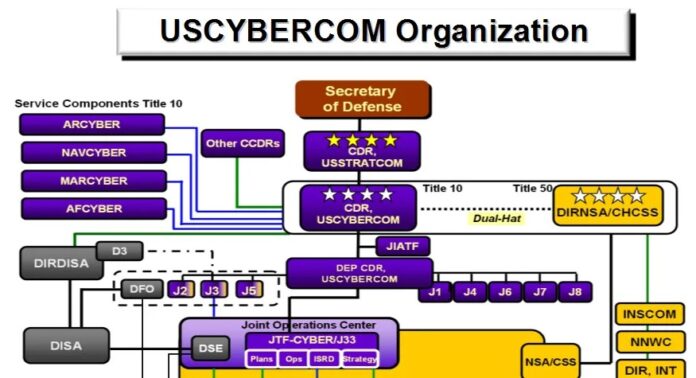
Organizational structure is an important element of any organization as it defines the hierarchy of authority, responsibility, and accountability within the organization. It is a framework used to define roles, responsibilities, and relationships between individuals and departments within the organization. It can also be used to identify areas of strengths and weaknesses within the company.
Organizational structure can be broken down into two types: functional and divisional structures. A functional structure identifies each position within an organization based on its specific purpose or task. This type of organizational structure is best suited for small businesses where there are limited resources available for management roles. A divisional structure divides departments into distinct segments based on their area of expertise or product offerings. This type of organizational structure works well in larger organizations with multiple departments with different functions that need to work together closely to achieve desired outcomes.
Organizational structures are designed to facilitate communication between employees, ensure clear lines of responsibility and accountability, promote efficiency among teams, encourage collaboration across departments and ultimately create a culture that encourages productivity and innovation throughout the entire organization.
Strategies for Defending the Nation from Cyberspace Attacks
The world has become more and more interconnected over the past few decades, and with that increased connectivity comes an increased risk of cyber attacks. Cyber attacks can be devastating to a nation’s infrastructure, economy, and security. As such, nations need to develop strategies for defending themselves from these types of malicious activities.
One essential strategy for defending the nation from cyberspace attacks is to ensure that all computer systems are regularly updated with the latest security patches and software updates. This ensures that any potential vulnerabilities or exploits are patched up as soon as they are discovered so that hackers cannot take advantage of them. Additionally, businesses should also invest in regularly scheduled cybersecurity audits to identify any potential weak points in their networks or systems.
Challenges Facing Cyber Command

The use of technology in the modern world has created a unique set of challenges for those responsible for protecting our security. Cyber Command is the United States’ unified command responsible for defending our cyberspace, and it faces a range of complex issues.
One major challenge facing Cyber Command is the changing nature of cyber threats. As technology evolves, so do the tactics used by malicious actors to gain access to sensitive information and systems. In addition, many cyber-attacks are now carried out using automated tools or scripts that can quickly spread across networks or move between computers with ease. This requires constant vigilance from Cyber Command to identify and respond to new threats as they emerge.
Another key challenge is combatting state-sponsored cyber-attacks. These attacks are often more sophisticated than those perpetrated by criminal organizations and pose a serious threat to national security. To counter such attacks, Cyber Command must have an understanding of both current capabilities and future trends to develop effective strategies for defense against them.
Conclusion
In conclusion, Cyber Command is a powerful tool that can be used to protect the world’s critical infrastructure and services against cyber threats. It provides an important layer of defense against malicious actors, who often try to target vulnerable areas such as government networks or private companies.
By having this command in place, organizations can be better prepared for potential cyber-attacks and can quickly respond if one does occur. Cyber Command is an invaluable asset to have in the fight against cybercrime, and its importance will only continue to grow as our digital world becomes more interconnected.